PKI Certificate Migration 2018
Please find below information related to activities needed as part of the migration to a new version of the PEPPOL PKI Certificate.
The short version
The OpenPeppol eDelivery Network is migrating to a new PKI infrastructure.
- After 2018-09-03 00:00:00 all Access Point Providers in the network MUST be able to support both the current PKI v2 certificates and the new PKI v3 certificates. Transactions can still be sent using EITHER v2 or v3 PKI certificates.
- After 2018-11-30 23:59:59 all Access Point Providers in the network MUST only send and receive transactions using the new PKI v3 certificates.
- The required Root and Intermediate CAs are available now for download here.
- You are encouraged to start enrolling for a PKI v3 certificate from mid-April 2018 in preparation for the September migration. The new PKI v3 certificates can be requested from PEPPOL Jira Service desk here: https://openpeppol.atlassian.net/servicedesk/customer/portal/1
Background
The migration is necessary and can not wait until the current PKI certificates expire, due to the following:
- Improved security. The current PKI infrastructure is based on SHA-1 cryptography, which was recently announced as not recommended for use, due to discovered exploits. The new PKI infrastructure will be based on certificates supporting SHA-256 cryptography which currently is the recommended web standard.
- Responsible organization. In the current PKI infrastructure, the issuing agency organization is "DIGST" (Danish Agency for Digitisation) and a request has been made to move this responsibility to the appropriate organization (OpenPEPPOL AISBL).
- Minor improvements. Some smaller changes to the naming conventions will make it easier to maintain the certificates and also to utilize a more cost effective pricing model which will be based on the member level rather than on the individual certificates.
Dictionary
| Term | Clarification |
|---|---|
AP | Peppol Access Point |
| SMP | Service Metadata Publisher |
| T1 | Date when PKI migration starts |
| T2 | Date when PKI migration ends |
| C1 | Internal date when issuing of PKI v3 certificates will commence |
| C2 | Internal date when PKI v2 certificates can no longer be issued |
| Exchange transactions | Ability for a PEPPOL Access Point to both send and receive transactions |
| PKI v2 Certificates | The PKI certificates that are currently in use, that we are migrating from |
| PKI v3 Certificates | The PKI certificates being implemented, that we are migrating to |
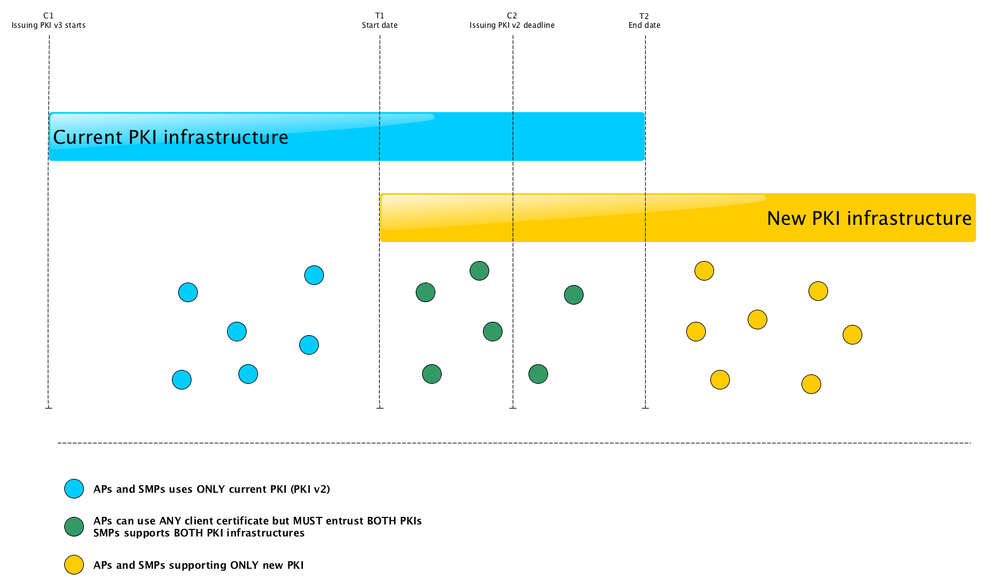
Process implementation and timeline
Refer to the graph below;
- After C1 the operational office of OpenPeppol will commence issuing of PKI v3 certificates.
- Up until date T1;
- All APs MUST be able to exchange transactions using the PKI v2 certificates.
- All SMPs MUST support PKI v2 certificates.
- SML MUST support PKI v2 certificates.
- PEPPOL Directory MUST support PKI v2 certificates.
- After date T1 and until date T2;
- All APs MUST be able to initiate a transaction (send) using ANY of the two available PKI certificates (v2 or v3).
- All APs MUST be able to support receiving transactions initiated using BOTH available PKI certificates (v2 and v3).
- All SMPs MUST support BOTH available PKI certificates (v2 and v3).
- Before C2;
- All (operational before T1) AP and SMP providers will have been issued certificates from the PKI v3 infrastructure (this is an internal OpenPeppol deadline).
- After date T2;
- All APs MUST only exchange transactions using PKI v3 certificates.
- All SMPs MUST only support PKI v3 certificates.
C1 = 2018-04-16 00:00:00
T1 = 2018-09-03 00:00:00
C2 = 2018-10-31 23:59:59
T2 = 2018-11-30 23:59:59
Technical implementation
How to implement this from a technical point of view is dependent on the AP or SMP platform used. There will not be a guideline available for every platform, but the general approach is as follows.
For AP providers;
- Before T1. Prepare your implementation so that it will be able to entrust transactions/signatures using the PKI v3 certificates.
- Between T1 and T2 (and before C1). You will be issued a client certificate from the PKI v3 infrastructure. For your Peppol Access Point implementation, replace the current client certificate with the new one. Any receivers (participants) you might have registered in an SMP must also be updated with the public key of the issued PKI v3 certificate.
- After T2. Patch your implementation so it no longer entrusts transactions/signatures using the current (then old) PKI certificates.
For SMP providers;
- Between T1 and T2. You will be issued a client certificate from the PKI v3 infrastructure. You will need to migrate the v2 SMP certificate in the SML to the v3 SMP certificate, the process for migrating the certificate has been digitalised and the official documentation of supported operations by the SML is available here. To migrate you will need to call interface UC12 - PrepareChangeCertificate.
The needed Root and Intermediate CAs are available for download here.
| Access Point | SMP | PEPPOL Directory | SML | OpenPEPPOL | |||
|---|---|---|---|---|---|---|---|
| Sending | Receiving | Server | Client | ||||
| No later than T1 |
|
|
|
|
| After T1 only v3 certificates will be issued. | |
| After C1 | All service providers should have a v3 certificate. | ||||||
| No later than T2 |
|
|
|
|
|
| |
| After T2 |
|
|
|
|
|
| |
How to act as a service provider?
Please refer to this matrix to identify which situation applies to you.
| Provider | In PROD before T1 | In TEST before T1 | In TEST after T1 | Enter TEST after T1 | Certificate expires before T2 | Certificate expires after T2 | Recommendation |
|---|---|---|---|---|---|---|---|
| AP/SMP | YES | - | - | - | YES | You will be prioritized in the process for being issued a PKI v3 certificate before T1. If you can't install it before end of expiry of PKI v2 certificates, then renew PKI v2 certificate and follow matching recommendation for that scenario. | |
| AP/SMP | YES | - | - | - | YES | Before C1 you will have been issued a PKI v3 certificate. Make sure to implement this certificate into your platform before T2. | |
| AP/SMP | - | YES | - | - | If you complete your tests and become eligible for a PROD certificate before T1. You will be prioritized in the process for being issued a PKI v3 PROD certificate before T1. | ||
| AP/SMP | - | YES | - | - | If you complete your tests and become eligible for a PROD certificate before T2, you will be issued a PKI v3 PROD certificate. If you fail to complete your tests before T2, you will have to reapply for a PKI v3 TEST certificate. | ||
| AP/SMP | - | YES | - | - | You will use a PKI v3 TEST certificate for your testing .You will be issued a PKI v3 PROD certificate when you complete tests and become eligible for a PROD certificate. |