Keep in mind that latest version of Firefox is not compatible with the enrollment process. Since Firefox by default is configured to auto-update, you might need to disable this feature before downgrading to a compatible version of the browser (to avoid Firefox auto-update after the installation is complete).
Prerequisites
This user guide starts when the PKI certificate request has been approved and the end user (OpenPeppol Member) has received the enrollment email (mail with subject 'Enroll for your (xyz OpenPEPPOL) certificate') and the SMS containing the enrollment email.
...
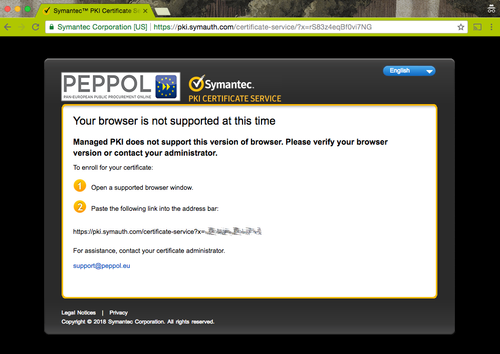
If your browser is unsupported you will see the following information if you try to start the enrollment process.
Issuing process
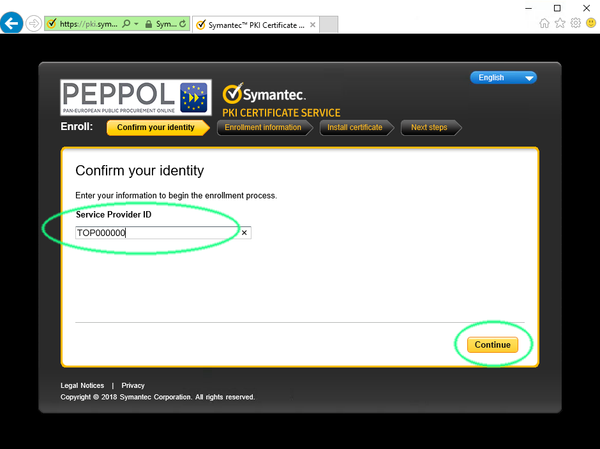
- Navigate your web browser to the link in your enrollment mail. You should be greeted with a page asking you to enter the 'Service Provider ID'.
Your assigned 'Service Provider ID' can be found in the enrollment mail. Please be aware of that if you are applying for multiple certificates then the same Service Provider ID will be reused for all your certificates.
Fill in your Service Provider ID and click continue. In the next step, refer to your received SMS that contains the enrollment code. If you have applied for multiple types of certificates, make sure you use the expected code for the current type of certificate you are enrolling for.
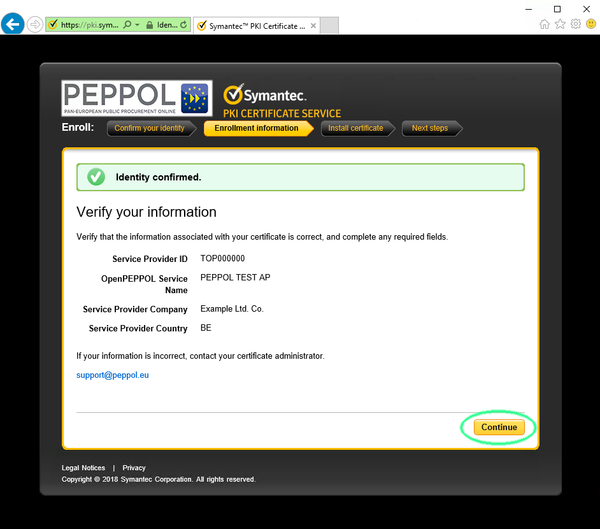
Enter the enrollment code and click continue.Next step will confirm whether you entered the expected details correctly.
Verify that the displayed information is correct and click continue.
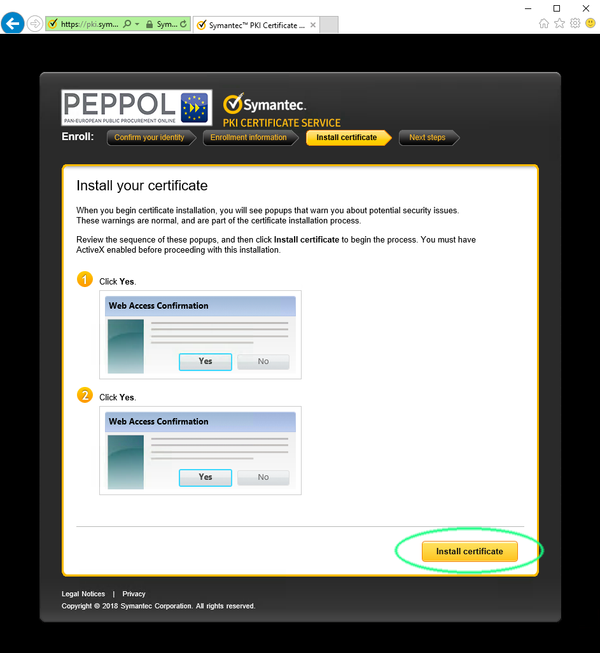
- You will now be informed about the certificate generation process.
Read through the information and click 'Install certificate'
The certificate will now be generated and installed in your web browsers keystore.
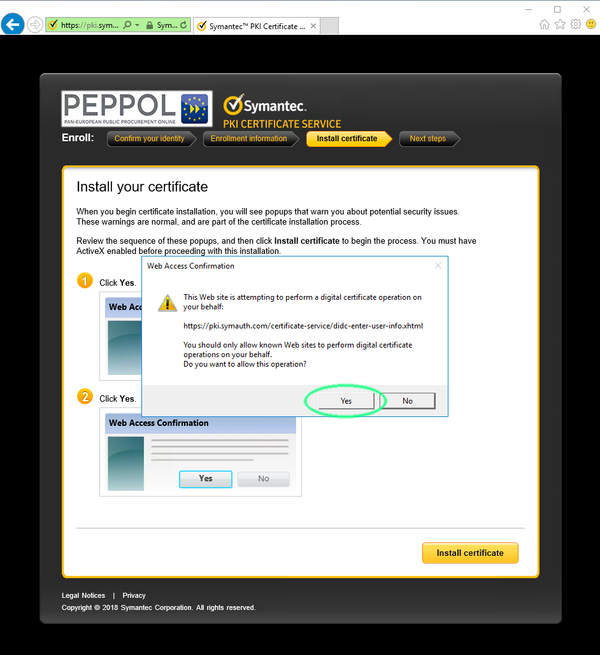
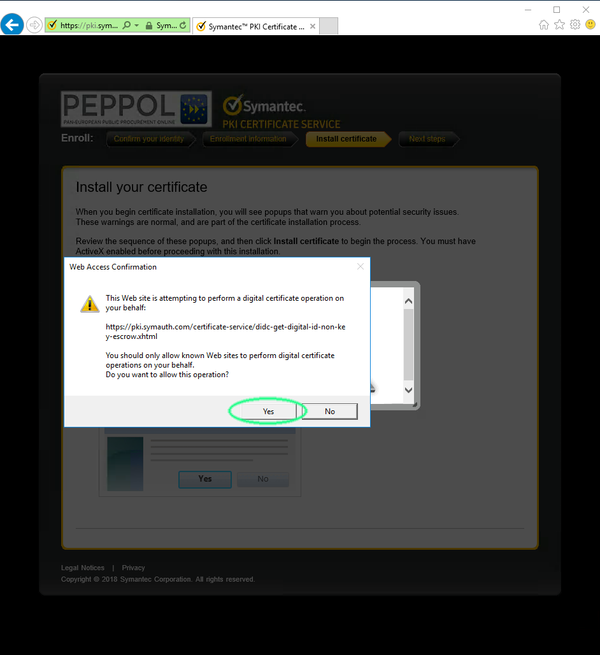
Click ok to confim During the process you will need to acknowledge two alerts.
Click 'Yes' to confirm and close the first alert.
Click 'Yes' to confirm and close the second alert.
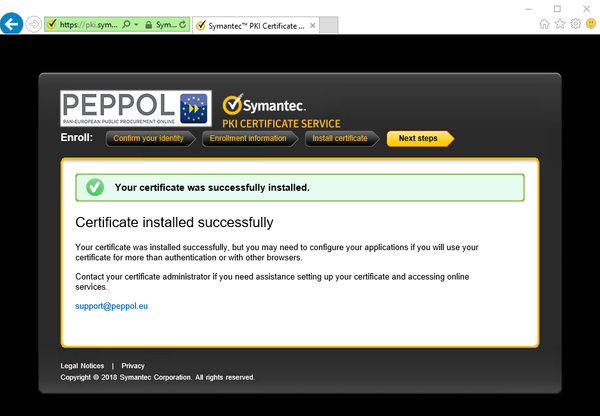
Your certificate has now been installed in the web browsers key store.
It is now safe to close the web browser tab you used for the certificate generation process.
Export the certificate
In order to use your certificate in your implementation you must export the certificate key-pair.
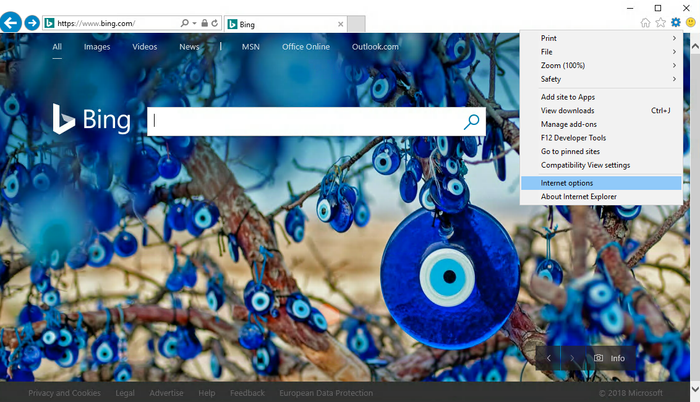
- In your web browsers browser (that you used during the enrollment) either , navigate to 'Preferences' and then click the 'Privacy & Security' tab, or enter the following URL manually 'about:preferences#privacy' and hit enter. Browse down to the Security section.
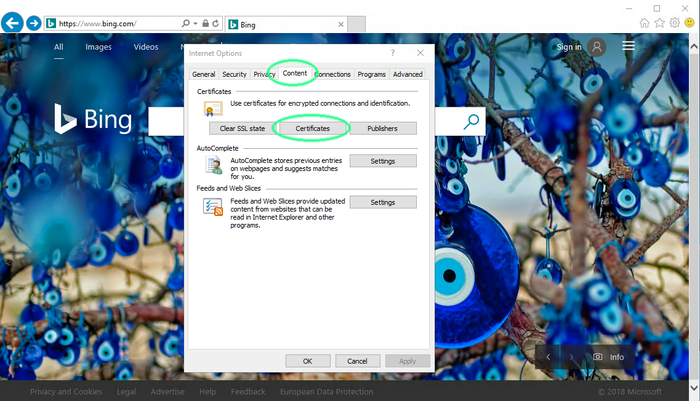
the menu.Click 'Internet Options'
An option pane will open.
Click the 'Content' tab, and then click 'Certificates'.
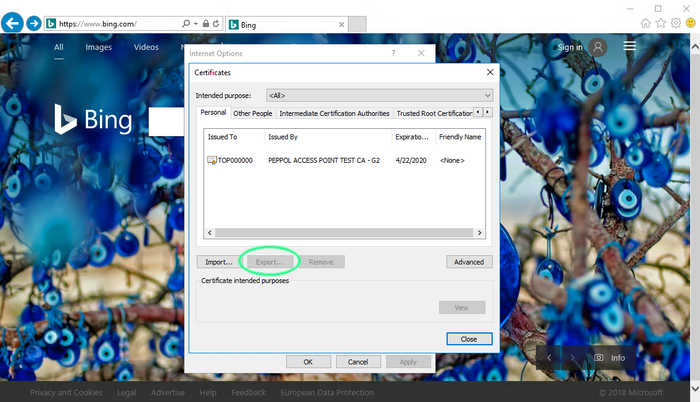
The next pane will list all installed certificates.
Choose the certificate you wish to export and click export.
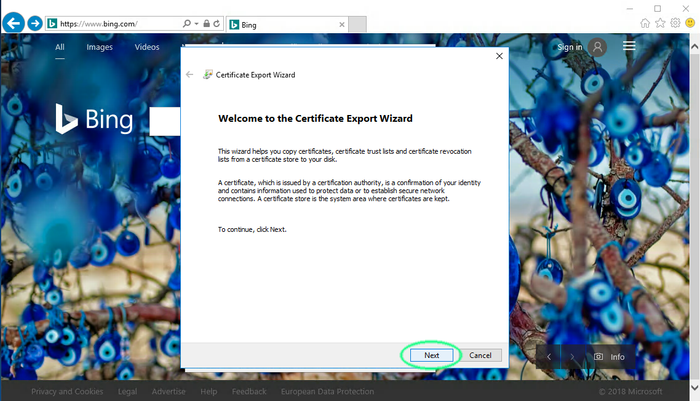
Click next.
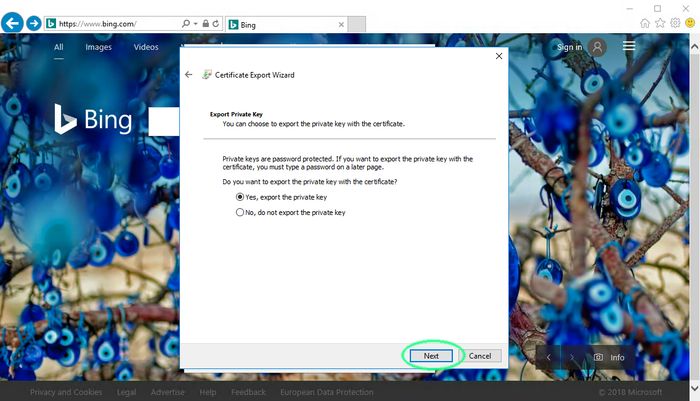
Confirm that you wish to export your private certificate
Click next.
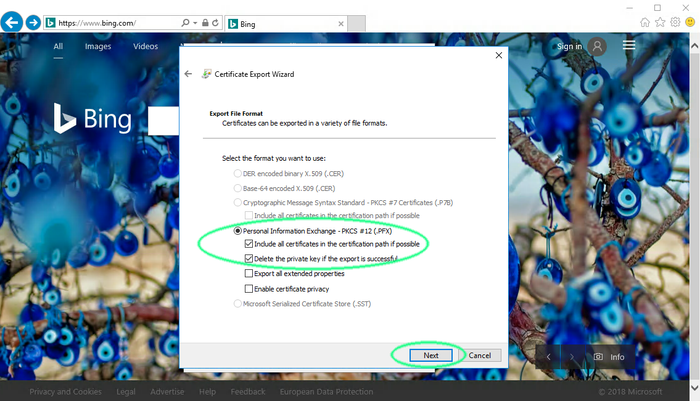
Choose the export options in the next pane.
The recommended format is PKCS 12 and to include the complete certificate chain if available. It is also recommended to delete the certificate from the web browser keystore once it has been successfully exported. Click next once the selections have been made.
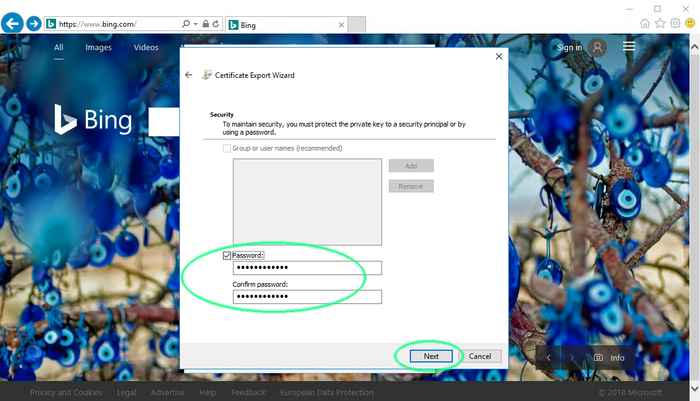
Choose password protection and pick a password
Click next.
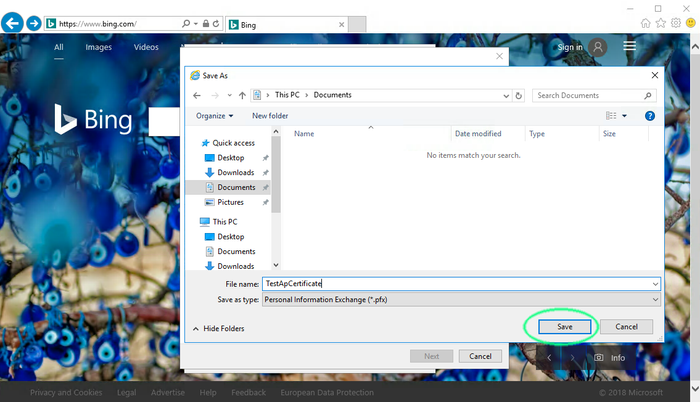
Pick a location to save your PKCS12-file
Click Save.
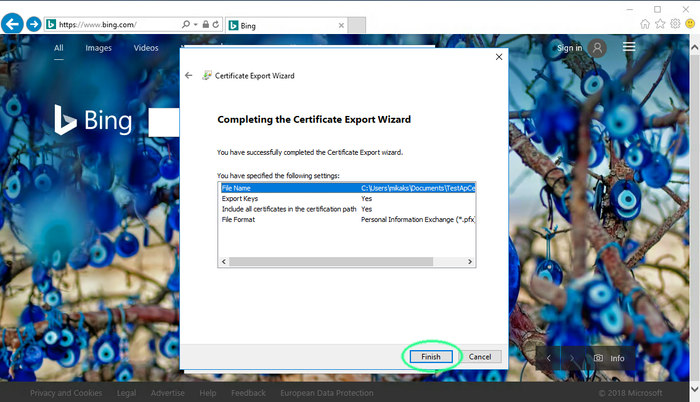
Verify all made settings
Click Finish.
- You have exported your certificate and it is ready to be used in your implementation. Make sure to verify that the certificate has been deleted from the web browser keystore to minimize risk of compromising the certificate.